Occasionally, running untrusted applications poses a dilemma. While Linux systems boast lower susceptibility to malware, they aren’t impervious. Whether visiting dubious websites or handling sensitive data like bank accounts, caution is warranted. Even trusted websites can harbor suspect browser add-ons or extensions.
In each case, sandboxing proves useful. The concept involves confining non-trusted applications within an isolated container – a sandbox – to prevent access to personal data or other system applications. While Sandboxie fulfills this role for Microsoft Windows users, Linux users can rely on Firejail.
Without delay, let’s explore how to install and utilize Firejail for sandboxing apps on Linux:
Install Firejail
For Debian, Ubuntu, or Linux Mint users, launch the Terminal and execute the following command:
[sourcecode]sudo apt install firejail[/sourcecode]
Enter your account password and press Enter. If asked for confirmation, type y and press Enter again.
If using Fedora or any other RedHat-based distribution, replace apt with yum:
[sourcecode]sudo yum install firejail[/sourcecode]
You are now ready to run Firejail.
Optional: Install the Graphical Interface
You can choose to install the official graphical front-end for Firejail, called Firetools. It’s not available in official repositories, so manual installation is required.
1. Download the installation file for your system. Debian, Ubuntu, and Mint users should download the file ending with .deb. On a 64-bit Mint installation, I selected firetools_0.9.40.1_1_amd64.deb.
2. After the download is complete, open the Terminal and navigate to your Downloads folder by running cd ~/Downloads.
3. Now install the Firetools package by running the command sudo dpkg -i firetools*.deb.
4. Enter your password, hit Enter, and you’re done.
Basic Usage
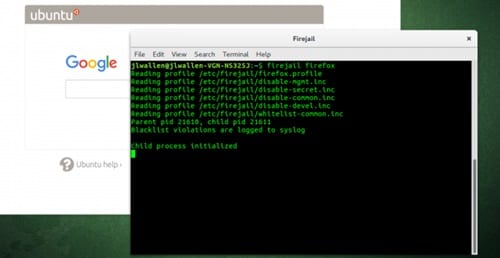
In a Terminal, write firejail, followed by the command you need to run. For instance, to run Firefox:
Ensure all Firefox windows are closed before proceeding. Otherwise, a new tab or window will open in the current session, nullifying any security benefits from Firejail.
Similarly, for Google Chrome:
Running commands like this grants the application access to only essential configuration directories and your Downloads folder. Access to the remaining file system and other directories in your Home folder is restricted. This is evident when attempting to access my home folder from Chrome:
Most of my folders, including Pictures and Documents, are inaccessible from the sandboxed Chrome. Attempts to access them by modifying the URL will result in a “File not found” error:
Further Application Restriction
Sometimes, you might need stricter controls. For instance, you may opt for a new browser profile with no history or add-ons. Suppose you also wish to block access to your Downloads folder. In that case, utilize the private option. Execute the application with:
[sourcecode]firejail google-chrome –private[/sourcecode]
This method fully restricts the application, ensuring it starts fresh without the ability to create or download files.
Using the Graphical Interface – Firetools
If you prefer a GUI over running commands manually, employ the graphical front-end for Firejail, Firetools. Launch Terminal and input firetools. A window similar to this will appear:
Double click any pre-configured application (Firefox and VLC here) to run it sandboxed. To add an application, right click an empty space on the Firetools app, and click Edit:
Enter the name, description, and command you want to run. The command is the same as in a console. For example, to create an icon for Google Chrome to run in private mode, input:
Now double-click the icon you created to launch the app:
Run Doubtful Applications Securely On Linux With Firejail
That’s it for sandboxing non-trusted apps in Linux with Firejail. To explore advanced sandboxing options, refer to the official documentation. How do you use Firejail? Share your experiences in the comments below.

Pritam Chopra is a seasoned IT professional and a passionate blogger hailing from the dynamic realm of technology. With an insatiable curiosity for all things tech-related, Pritam has dedicated himself to exploring and unraveling the intricacies of the digital world.